Wpa2 Personal Or Wpa2 Enterprise
WPA2 Enterprise uses IEEE 802.1X, which offers enterprise-grade authentication. WPA2 Personal uses pre-shared keys (PSK) and is designed for home use. However, WPA2 Enterprise is specifically designed for use in organizations.Benefits of WPA2 EnterpriseThough WPA2 Personal is easier to deploy and use than WPA2 Enterprise, it is not the most. The Wi-Fi Protected Access is a wireless technology designed to secure the communiciations between stations and the Access Point from eavesdropping and tampering attacks. It is defined in 802.11i standard and has been adopted in home, small business (WPA2-Personal) and enterprises (WPA2-Enterprise) since 2004. WPA2 is the next generation of Wi-Fi security. It is the Wi-Fi Alliance's interoperable implementation of the ratified IEEE 802.11i standard. It implements the National Institute of Standards and Technology (NIST) recommended Advanced Encryption Standard (AES) encryption algorithm using Counter Mode with Cipher Block Chaining Message Authentication Code Protocol (CCMP).
Many routers provide WPA2-PSK (TKIP), WPA2-PSK (AES), and WPA2-PSK (TKIP/AES) as options. Choose the wrong one, though, and you’ll have a slower, less-secure network.
Wired Equivalent Privacy (WEP), Wi-Fi Protected Access (WPA), and Wi-Fi Protected Access II (WPA2) are the primary security algorithms you’ll see when setting up a wireless network. WEP is the oldest and has proven to be vulnerable as more and more security flaws have been discovered. WPA improved security, but is now also considered vulnerable to intrusion. WPA2, while not perfect, is currently the most secure choice. Temporal Key Integrity Protocol (TKIP) and Advanced Encryption Standard (AES) are the two different types of encryption you’ll see used on networks secured with WPA2. Let’s take a look at how they differ and which is best for you.

AES vs. TKIP
TKIP and AES are two different types of encryption that can be used by a Wi-Fi network. TKIP is actually an older encryption protocol introduced with WPA to replace the very-insecure WEP encryption at the time. TKIP is actually quite similar to WEP encryption. TKIP is no longer considered secure, and is now deprecated. In other words, you shouldn’t be using it.
AES is a more secure encryption protocol introduced with WPA2. AES isn’t some creaky standard developed specifically for Wi-Fi networks, either. It’s a serious worldwide encryption standard that’s even been adopted by the US government. For example, when you encrypt a hard drive with TrueCrypt, it can use AES encryption for that. AES is generally considered quite secure, and the main weaknesses would be brute-force attacks (prevented by using a strong passphrase) and security weaknesses in other aspects of WPA2.
The short version is that TKIP is an older encryption standard used by the WPA standard. AES is a newer Wi-Fi encryption solution used by the new-and-secure WPA2 standard. In theory, that’s the end of it. But, depending on your router, just choosing WPA2 may not be good enough.
While WPA2 is supposed to use AES for optimal security, it can also use TKIP where backward compatibility with legacy devices is needed. In such a state, devices that support WPA2 will connect with WPA2 and devices that support WPA will connect with WPA. So “WPA2” doesn’t always mean WPA2-AES. However, on devices without a visible “TKIP” or “AES” option, WPA2 is generally synonymous with WPA2-AES.
RELATED:Warning: Encrypted WPA2 Wi-Fi Networks Are Still Vulnerable to Snooping
And in case you’re wondering, the “PSK” in those names stands for “pre-shared key” — the pre-shared key is generally your encryption passphrase. This distinguishes it from WPA-Enterprise, which uses a RADIUS server to hand out unique keys on larger corporate or government Wi-Fi networks.
Wi-Fi Security Modes Explained
Confused yet? We’re not surprised. But all you really need to do is hunt down the one, most secure option in the list that works with your devices. Here are the options you’re likely to see on your router:
RELATED:Why You Shouldn’t Host an Open Wi-Fi Network Without a Password
Wpa2 Personal Or Wpa2 Enterprise System
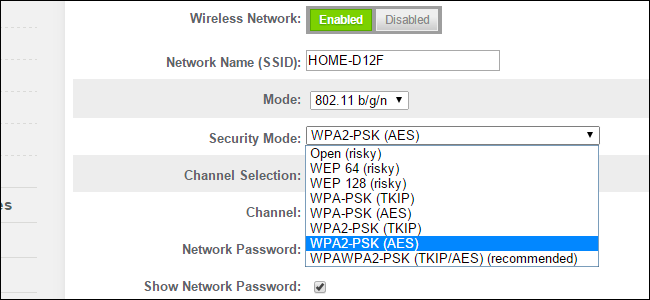
- Open (risky): Open Wi-Fi networks have no passphrase. You shouldn’t set up an open Wi-Fi network—seriously, you could have your door busted down by police.
- WEP 64 (risky): The old WEP protocol standard is vulnerable and you really shouldn’t use it.
- WEP 128 (risky): This is WEP, but with a larger encryption key size. It isn’t really any less vulnerable than WEP 64.
- WPA-PSK (TKIP): This uses the original version of the WPA protocol (essentially WPA1). It has been superseded by WPA2 and isn’t secure.
- WPA-PSK (AES): This uses the original WPA protocol, but replaces TKIP with the more modern AES encryption. It’s offered as a stopgap, but devices that support AES will almost always support WPA2, while devices that require WPA will almost never support AES encryption. So, this option makes little sense.
- WPA2-PSK (TKIP): This uses the modern WPA2 standard with older TKIP encryption. This isn’t secure, and is only a good idea if you have older devices that can’t connect to a WPA2-PSK (AES) network.
- WPA2-PSK (AES): This is the most secure option. It uses WPA2, the latest Wi-Fi encryption standard, and the latest AES encryption protocol. You should be using this option. On some devices, you’ll just see the option “WPA2” or “WPA2-PSK.” If you do, it will probably just use AES, as that’s a common-sense choice.
- WPAWPA2-PSK (TKIP/AES): Some devices offer—and even recommend—this mixed-mode option. This option enables both WPA and WPA2, with both TKIP and AES. This provides maximum compatibility with any ancient devices you might have, but also allows an attacker to breach your network by cracking the more vulnerable WPA and TKIP protocols.
WPA2 certification became available in 2004, ten years ago. In 2006, WPA2 certification became mandatory. Any device manufactured after 2006 with a “Wi-Fi” logo must support WPA2 encryption.
Since your Wi-Fi enabled devices are most likely newer than 8-10 years old, you should be fine just choosing WPA2-PSK (AES). Select that option and then you can see if anything doesn’t work. If a device does stop working, you can always change it back. Although, if security is a concern, you might just want to buy a new device manufactured since 2006.
Wpa2 Personal Or Wpa2 Enterprise
WPA and TKIP Will Slow Your Wi-Fi Down
RELATED:Understanding Routers, Switches, and Network Hardware
WPA and TKIP compatability options can also slow down your Wi-Fi network. Many modern Wi-Fi routers that support 802.11n and newer, faster standards will slow down to 54mbps if you enable WPA or TKIP in their options. They do this to ensure they’re compatible with these older devices.
By comparison, even 802.11n supports up to 300mbps if you’re using WPA2 with AES. Theoretically, 802.11ac offers maximum speeds of 3.46 Gbps under optimum (read: perfect) conditions.
On most routers we’ve seen, the options are generally WEP, WPA (TKIP), and WPA2 (AES)—with perhaps a WPA (TKIP) + WPA2 (AES) compatibility mode thrown in for good measure.
If you do have an odd sort of router that offers WPA2 in either TKIP or AES flavors, choose AES. Almost all your devices will certainly work with it, and it’s faster and more secure. It’s an easy choice, as long as you can remember AES is the good one.

Image Credit: miniyo73 on Flickr
READ NEXT- › How to Stream UFC 239 Jon Jones vs. Santos Online
- › How to Check Your Wi-Fi Signal Strength
- › What Is “Upscaling” on a TV, and How Does It Work?
- › How to See the Applications Using Your Network on Windows 10
- › How to See All Devices on Your Network With nmap on Linux